The Zlib library is a general purpose data compression library compatible with the gzip format. The code is thread safe, assuming that the standard librar y functions used are thread safe, such as memory allocation routines. It provides in-memory compression and decompression functions, including integrity checks of the uncompressed data.
Photo Pos Pro photo editor is the best totally free Photo Editor and Image Editor (free Photo editing and Image editing software). The software allows you easily create, edit, enhance, print, and manipulate your digital photos and computer graphics, and easily create eye-catching graphics, beautiful collages, greeting cards, business cards, website designs, buttons and much more. Though the Photo Pos Pro photo editor is a powerful program, it contains an extremely user-friendly interface enabling you to work intuitively. The photo editor includes complete help system, free step-by-step tutorials and Hundreds of pre-made templates, vectorial objects, photo frames, patterns, textures, styles and shapes--all to accelerate your work and make it fun and easy. Photo Pos Pro supports many image file types, transparent GIF's and PNG's, multiple-image printing; tabbed workspace; advanced enhancing, editing and computer graphics; special effects; layers, vectorial objects, masks, script and batch tools;brushes & dynamic brushes;green/blue screen tool; a batch converter and Web development tools including HTML Wizard that allows easily converting your designs into Web Pages with cool effects (no HTML/Java knowledge needed).. If you are a beginner you can easily begin to use the digital photo editor in an intuitive fashion, using the help guide will help you to become a pro!. If you are an experienced user, you will probably be amazed to discover the infinite possibilities which this photo and image editing software has to offer in the fields of Digital Image Enhancement and Computer Graphics.
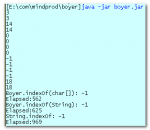
Fast string search (indexOf) using the Boyer-Moore algorithm. Incorporate this class into your own Java programs to rapidly search strings. Boyerr-Moore is about twice as fast as String.indexOf when the string you are searching in is 2K or over and the pattern you are searching for is 4 characters or longer.
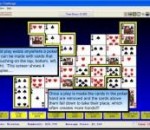
This enjoyable, easy-to-learn card game cleverly blends the rules of poker with solitaire. The object of the game is to identify poker hands within a deck of cards that has been dealt and evenly spread out face up. Once a hand has been marked to play, the cards that make up the hand are removed, points are awarded, and any cards above them fall down to take their place. (The game's screen shot shows an example of the concept). It will challenge you over and over with countless possibilities of play, as each deal is unique, and there are many different ways to complete a game. Once all play possibilities have been exhausted, the game will automatically end and calculate your score with exciting special effects. In fact, in addition to the concept of the game itself, it will be sure to entertain you with windows that snap, pop, slide, and explode on and off screen. Game rules are presented when the game starts (and in just one screen of information) so that you will find yourself actively playing the very first hand dealt. As your skills advance, you will be challenged to think several moves ahead to build more (and better) poker hands within the set of constantly shifting cards. The challenge continues as you're awarded bonus points for creating as many different hands as possible, for finding poker hands that yield the most points, and for removing as many cards as you can. To add yet another strategic element to the game, you are initially given a timer bonus that slowly ticks away to reward quick completion of each game. To help you better measure your skills, the game tracks account balances, average scores, and high scores. Are you ready for the challenge?
RRT is a set of handy tools that scans, remove and re-enables all what a virus had previously disabled (System Restrictions) and gives you back the control over your own computer, common behavior of a virus is to make some changes to the system restrictions in order to hide itself from easy detection, these restrictions are most often: - Disable Folder Options >> so the user can't set the option to show hidden files! - Disable Registry Tools >> so the user can't see what is going on during system startup! - Disable Ctrl+Alt+Del >> so the user can't see the virus and the other applications running! RRT also protects you from any further infections that come from removable media (Pen Drives). Since we noticed that most of the malware nowadays spread via removable media (Flash disks in specific), we implemented RRT with the ability of monitoring, blocking and removing any type of malware that uses flash disks to spread. RRT with AutoRemove enabled will monitor your system and detects any flash disk as soon as it gets plugged into the USB port. The generic technique will work in less than few milliseconds , if it detects any infection in the flash disk, it will block it and remove the infection before it makes any harm to your computer. The great news is that RRT -unlick the traditional AVs- doesn't need to be updated with malware signatures in order for it to do it's job, instead, it uses a generic and smart technique that detects any type of malware that attempt to infect your system via flash disk inserted into the USB ports. Beside the heuristic scanner, RRT includes a traditional scanner and remover for malware. It also includes a smart malware activities recognition technique and a malware signatures database you build yourself.
Complete protection against viruses and Internet attacks for Windows x64 computers Why Use Comodo Internet Security? Comodo Internet Security for Windows x64 is the free, multi-layered security application that keeps hackers out and personal information in. Built from the ground upwards with your security in mind, CIS offers 360° protection by combining powerful Antivirus protection, an enterprise class packet filtering firewall, and an advanced host intrusion prevention system called Defense+. Unlike the stripped down versions of commercial software that other software vendors offer for free, this is the full, completely functional version of the product. Alternatively, users can upgrade to CIS Pro for just $49 per year and receive two additional services—LivePCSupport (Total Security & Support Package)—a 24 hour per day, unlimited incident support services package which usually markets for $99 per year and TrustConnect - a secure Internet proxy service that ensures 128 bit encrypted connectivity from any public wireless hot-spot. CIS Includes: * Firewall: Slam the door shut on hackers and identity thieves. * Antivirus: Track down and destroy any existing malware hiding in a PC. * Defense+: Protects critical system files and blocks malware before it installs. * Memory Firewall: Cutting-edge protection against sophisticated buffer overflow attacks. * Anti-Malware Kills malicious processes before they can do harm. Features: * Antivirus, Anti-Spyware, Anti-Rootkit & Bot protection * Defends your PC from Internet attacks * Detects and eliminates viruses * Prevents malware from being installed * Auto Sandbox Technology™ * Easy to install, configure and use * Free to both business and home users What makes Internet Security different? Default Deny Protection™ (DDP) Only known and listed PC-safe files and applications are able to access your PC. Prevention-based protection Firewall and Antivirus combine to stop viruses and malware before they enter the PC. Personalized protection alerts Firewall quickly learns the rules you set for downloading software, and adjusts its alerts accordingly to fit your needs. Real-time access to updated virus definitions Automatic updates mean greatest possible protection possible against zero-day threats. One-click virus scanning Make sure your PC is clean with one simple button click. Uncluttered, user-friendly interface Quickly navigate through the various parts of Firewall protection without getting lost. Thorough security "wizards" Preset security settings for simple point-and-click setup. Unique "slider" to easily change your current security level Easily switch between presets to reflect your security preference at any given time. Exclusive access to Comodo's "safe-list" List of over two million known PC-friendly files and applications so safe files and apps are allowed to run.
AccdbMerge is easy to use diff & merge tool for Microsoft Access *.mdb and *.accdb files. This tool allows to compare and import/export database objects between two files.
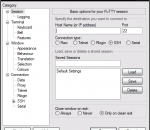
portable telnet and SSH PuTTY Portable is the popular PuTTY telnet and SSH client packaged as a portable app, so you can connect in to your systems on the go. You can place it on your USB flash drive, iPod, portable hard drive or a CD and use it on any computer, without leaving any personal information behind. Features: PuTTY is a lightweight telnet and SSH client for Windows, along with an xterm terminal emulator. It allows you to securely connect to your systems while on the go. Advanced Tip - If you'd like a high-color icon and transparency, PuTTY Portable is designed to work with PuTTY Tray, too. Just replace putty.exe in the PuTTYPortableAppputty directory with the PuTTY Tray executable.
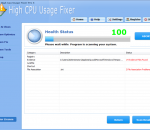
Download High CPU Usage Fixer, the World's most comprehensive computer error fixer and Windows registry cleaner and fix a significant number of Windows registry problems thoroughly! You will enjoy many automatic fixes and can manually fix all system problems! High CPU Usage Fixer is a great program that you should use to clean your PC and to improve usability and performance just with a few clicks.
Total Commander 64-bit (former Wincmd) is an Explorer replacement for Windows. Total Commander handles archives like subdirectories. It supports ZIP/ARJ/LHA/RAR/UC2/TAR/GZ/CAB/ACE archives, and has an internal ZIP-compatible packer. The search function allows to search for files inside archives, even for text.
Add multiple PST files into Outlook easily. Now with the help of ADDPST software users can import multiple PST files into Outlook or orphaned PST files which are stored in different locations and can put them consecutively at one place. By putting PST file at one location the hectic research work of Outlook users will become smoother. Know more: homepage
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.