Remo Outlook Backup and Migrate software helps you backup and restore Outlook emails along with all other Outlook attributes like email folders, contacts, calendar items, journal entries, tasks, notes, RSS feeds, settings, rules, E-mail accounts, junk e-mail lists and signatures. You can migrate Outlook data and settings from older version to a newer version of Outlook or from Windows XP / Vista to Windows 7.
HDDScan is a for hard drive diagnostics (RAID arrays, Flash USB and SSD drives are also supported). The program can test storage device for errors (Bad-blocks and bad sectors), show S.M.A.R.T. attributes and change some HDD parameters such as AAM, APM, etc. HDDScan is an application for low-level HDD diagnostics.
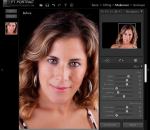
Easy portrait editing software, remove blemish and wrinkles, gain a perfect look. Support working as a Photoshop & Photoshop Elements plug-in. 1.Skin blemishes removal Quickly remove skin blemishes such as acnes, moles, redness, etc. Dramatically reduce wrinkles, eye bags, skin blotchiness and deep pores. Maintain nature skin texture so the portrait doesn't look over retouched. 2.Skin smoothing and enhancement Smooth skin, fine facial shine and enhance skin tone to give the portrait a professional look. 3.Features enhancement Remove red - eye, enhance eyes and eyebrows instantly. Whiten teeth and make lips look more vivid. 4.Face reshaping Reshape face, eyes, nose and mouth simply by moving sliders. Give the portrait a better look. 5.Full-body skin perfection With the skin brush you can customize the skin area easily to perfect all visible skin, not just the facial area. 6.Image color correction Remove color casts and adjust overall image color to restore a real photographic scene. 7.Formats supported Support importing file in these formats: Bitmap, JPEG, 24/48-bit TIFF, Camera RAW and Adobe DNG. Support saving as TIFF and JPEG.
IP Changer allows you to change the IP Address SubNet Mask Gateway DNS Server DHCP Status of your LAN Interface. You can save a set of settings for future usage or if you are frequently changing sites using your Laptop and do not want to remember for each site the exact IP configuration.
Bidder Robot is an application that makes it easy for you to automate clicks on a web site. Let's say you're on a live bidding site and you wish to bid on an item every time there is 20 seconds left and you don't want to sit in front of your computer for hours, then you can use Bidder Robot to help you bid for extended periods of time. How Does it work? It works very easily. You browse to the site where you do your bidding. Specify the area you want the bidder to watch and monitor (such as time remaining) Specify the value that should trigger a mouse click Click START After hitting start, the application will send a mouse click every time the trigger condition is met. If you're trading or bidding, it works. Who it is for It's for anybody that wishes to automate clicks on a computer based on changing values on a page.
SpeedConnect Internet Accelerator is a powerful Windows application designed to optimize and speed up your internet related activities including browsing, downloading, uploading, streaming, online gaming, sending and receiving email. Optimization is applied to several network related parameters, in order to prevent the data fragmentation and to improve the data throughput. All this translates into a faster internet connection: faster browsing, faster download, faster email and faster online gaming.
Create professional slide shows without any trade-offs for DVD and PC. Rotate pictures, collages, particles and texts, set transitions and zoom effects, animate using camera pans and movement paths. New! integrate your own video clips in the slide show. Stack and animate pictures with transparency. High-definition WMV output according HD-DVD standard, more than 100 text effects with Unicode support for exotic languages and fonts. Story board and timeline bring structure in your shows. The SlideShow-Master creates slide shows from theme presets in 3 clicks. The new support for multi-core processors puts some heat on your show. The direcX support boosts the performance. Where other programmes stop, SlideShow Studio takes off and it is easy to handle, nevertheless. Sort your photos, music and sounds in the timeline in any number of tracks, or gain an overview with the story board. Create parallel sequences and collages. For example, three images may fly over the screen at once, while a camera pan runs in the background and your film title that rolls onto the screen. Use animated transparency effects for images and texts. Dub your photos via microphone. Chapters help structure even large slide shows. Use EXIF-Data from the images of your digital camera for sorting and editing your photos, e.g. the capture date, time and more. Replay your slide shows in highest quality and great solution on the PC or through a beamer or burn a DVD or (S)VCD utilizing the integrated burn engine. For your creativity the sky is the limit. Example slide shows and extensive step-by-step tutorials will familiarize you with the vast functionality of AquaSoft SlideShow Studio. Benefit from more than 10 years of experience in slide show software development and become your own director.
Please take a closer look at Photoshop Fix Toolbox if you encounter data corruption issues affecting the integrity of Adobe Photoshop files. This program runs under all supported software environments and opens any version of PSD file for analysis. There is no need to worry about the safety of processed documents during the recovery of Adobe Photoshop images, this tool works with copies only, it does not affect original files. Please open the website of application developer and look through the specifications of Photoshop Fix Toolbox, make sure it may work on any PC in the network, including your own workstation. The efficiency of Adobe Photoshop recovery program remains the same on all computers, but it works slower on older workstations therefore you may need to install this application on a later PC to improve the speed of analysis. After the first start of Photoshop Fix Toolbox you may look at the interface of Adobe Photoshop recovery tool and evaluate its ease. The absence of additional settings allows starting the analysis of PSD files immediately, you may call the open file dialog, find a file of Adobe Photoshop format to be processed and click the Next softkey to start the analysis of selected PSD file. After the start of Photoshop fix process you may need to wait for a while because the parsing of selected image may be time consuming if the size of selected PSD document is too large and it is parsed on a slower computer. There are no other ways to improve the speed of analysis except installing this application on more powerful workstations so please be patient and wait for the end of data recovery process. As soon as the parsing of selected document is successfully completed, you may evaluate the efficiency of Adobe Photoshop recovery by previewing the results of analysis. In the end of PST repair our customers can export the data into new documents of Adobe Photoshop format. The last step is not available until you register Photoshop Fix Toolbox.
It’s always been our philosophy at AVG that everyone has the right to basic computer security at no charge. And our 80 million users think we’re doing a pretty good job. So if you’re planning to spend time online and you regularly exchange files with friends, check us out. * Surf, and search with confidence, while LinkScanner® keeps you safe from harmful sites * Get online and offline protection from viruses, spyware, and other nasties * Enjoy consistently high-speed PC performance with our new enhanced virus scanner * Automatic updates keep your protection current * Compatible with Windows XP, Vista, and Windows 7 AVG Anti-Virus Free Edition is an anti-virus protection tool available free of charge to home users. Rapid virus database updates are available for the lifetime of the product, thereby providing the high level of detection capability. The new 9.0 edition is faster, safer and easier to use. AVG Anti-Virus Free Edition gives you free rock solid protection for your basic security needs. The combined anti-virus/anti-spyware scanner in AVG Anti-Virus Free Edition runs up to 50% faster than earlier versions and doesn't get in your way. AVG Anti-Virus Free Edition also delivers new anti-phishing detection techniques, which can quickly and accurately determine whether or not a web page is hosting a phishing attack. Additionally, version 9.0 comes with basic anti-rootkit protection to ensure protection against sophisticated hidden threats. Features: · Surfing and searching the web and in your social networks LinkScanner Active Surf-Shield: · Ensures every web page you visit is safe – even before you go there. LinkScanner Search-Shield: · Applies safety ratings to your Google, MSN and Yahoo search results. Phishing Protection: · Checks to make sure web pages really are what they appear to be. · Emailing, Instant Messaging and downloading music and files E-mail Scanner: · Keeps you safe from dangerous attachments and links in your e-mail. · Whether you’re online or offline Anti-Virus: · Makes sure you can’t get or spread a virus, worm, or Trojan horse. Anti-Spyware: · Prevents unauthorized information access by spyware and adware. Basic Anti-Rootkit protection: · Ensures basic protection against sophisticated hidden threats. Update Manager: · Makes sure you’re always safe from the latest threats – automatically.
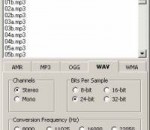
The AudioCommander software includes a powerful AMR converter feature that can convert from CD, MP3, WAV, WMA, OGG, AAC, AC3, AIFF, AU, VOX, RAW, PCM, ADPCM, A-LAW, u-LAW, MP2, FLAC, ALAC, CD, M4A, MP4, WavPack, AVI audio, other AMR file variations, etc. to AMR quickly and easily. AudioCommander can also convert AMR to MP3, WMA, WAV, OGG, AAC, ADPCM, AIFF, AMR, A-LAW, u-LAW, or VOX with the same ease. To begin using the software's AMR conversion feature, select the files you wish to convert using the "Add Files" link or click Add from the Edit menu. If converting to AMR, select the AMR tab, from which you can set the output AMR frequency and bitrate. Otherwise, select the appropriate tab for the desired output format, and choose the settings specific to that format. When you're ready to perform the AMR conversion, click the Start button. The conversion is performed in batch mode, which means that you can easily convert an entire list of audio files to and from AMR with very little effort. You can also convert the compression for AMR files, such as converting from one AMR bitrate to another. Sample AMR conversions include WAV to AMR, AMR to WAV, MP3 to AMR, AMR to MP3, WMA to AMR, AMR to WMA, etc.
IZArc2Go is portable version of IZArc. Just drop it on any USB Flash Drive and you will have full functional archive utility wherever you go. You don't have to install anything on the computer's hard disk. IZArc2Go has all features of IZArc except that it can’t be integrated into the Explorer shell menu and it is not possible to associate any archive file type with it.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.