Type like a pro by using a mouse or touch screen! Hot Virtual Keyboard makes previous-generation on-screen keyboards look ancient. Type faster with configurable mouse gestures, launch programs, browse the Internet, and run programmable macros with any of the 70 keyboards included with Hot Virtual Keyboard. The new on-screen keyboard employs advanced typing techniques used in modern mobile phones and communicators such as word auto-complete.
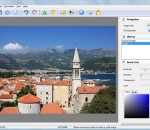
Home Photo Studio is a powerful, fun and easy photo editing program offering a complete set of image manipulation tools. Thanks to a convenient interface and a detailed help system, the software is simple to learn but provides enough options to keep any photo enthusiast creatively occupied. With Home Photo Studio, you can view and edit your digital shots. Photos can be retouched, color can be enhanced, red eye can be removed, and blurred images can be made clearer. All of these changes can be made with a click of the mouse! You can add special effects to your photos, including lighting, weather effects, and even 3D composition - a feature not commonly found on non-professional photo editing programs. Frames in a wide range of styles can be added to the photos, as well. When the photos have been enhanced, they can be used to create slide shows, postcards, and collages, which can be shared with others. This photo editing software includes hundreds of special effects, design templates, and project options that can be used with digital photos on computers. If mistakes are made during the editing or enhancing process, the multi-undo feature makes correcting the error easier. Additional features found in the software include the ability to quickly view EXIF data and to use plastic effects on photos. Users will appreciate the detailed help system built into the program so they can find answers when having trouble with a new project. Home Photo Studio provides all of the features and extras needed to modify and enhance digital images.
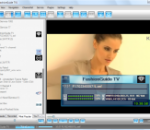
ProgDVB and ProgTV is two is 2 independent user interfaces which can work together from one folder at one list of channels, settings etc. ProgTV is aimed at use with remote control(HTPC). ProgDVB contains more functions but is intended for use by a mouse. Thus it is very convenient to use both interfaces. ProgDVB is a piece of software which allows you to watch SAT-Television and listen to Radio channels directly from satellite by using DVB-PCI cards with hardware decoders on the board, SAT-dish, and personal x86-compatible computers. Support for various types of data sources: * Internet TV and Radio. About 4000 channels in the list. * DVB-S (satellite), DVB-S2, DVB-C (cable), DVB-T, ATSC, ISDB-T * IPTV * Analog TV * Playback from a file Main functions: * High Definition TV support including H.264/AVC * Picture-in-picture support as well as independent simultaneous recording/playback of several channels from one or more devices * Support for the majority of DVB, ISDB-T and ATSC devices including DiSEqC and CAM interfaces support * Support for all digital TV audio formats: MPEG, AC3, AAC,... * Time shifting functionality using the RAM or disk buffer of unlimited size * 10 Bands equalizer * TV and Radio channels recording * Playback from disk based files * Electronic program guide (EPG) from Digital TV or XmlTV,JTV. * Teletext * Subtile(Teletext, image-based and closed captions) * Support for VR, VMR7,VMR9 and EVR renderers including OSD (except VR) independently from channel type or signal presence * Network broadcasting * Skins for OSD and GUI * Both Win32 and full-fledged Win64 versions are available * Interface Language Localizations Currently works with DVB-S, DVB-S2, DVB-T and DVB-C cards of the following manufactures: * Anysee (E30S Plus,...) * AverMedia DVB-S * Azurewave (TwinHan) (VP-1027, VP-1034, VP-1041,... ). * BroadLogic 2030/1030 * Compro VideoMate DVB-S * Digital everywhere FireDTV/FloppyDTV * DVBWorld USB2.0 DVB-S/DVBWorldDTV(PCI-Sat), Acorp TV878DS/DS110/DS120, Nextorm NBS240/NSC120 * GeniaTech products(Digistar DVB-S PCI, satbox, TVStar, Digistar2, Digiwave 103G,...) * Hauppauge * Kworld DVB-S 100 compatible (Vstream, Dynavision..... ) * LifeView FlyDVB * 10moons * Netcast DVB * NEWMI Advanced DVB * Pinnacle * Technotrend * Tevii * TBS Q-Box * Technisat * Telemann Skymedia 300 DVB (not official) * Tongshi * Terratec * St@rKey usb box * Cards with BDA driver (possible issues with some cards) * Also works without a card, for example, as a video player or as a broadcast client
Easy Karaoke Player plays karaoke, records karaoke song to wav file. Easy Karaoke Player can play all kinds of multimedia files with a build-in powerful multimedia player. Easy Karaoke Player plays many audio formats such as MP3, MIDI, KAR, WAV, WMA, AC3, OGG, MPA, MP2, AU, AIF, SND, etc., and video formats VCD, MPEG, AVI, WMV, ASF, OGM, DIVX, DAT, SVCD etc. You can sing your favorite song and record it to high quality WAV file. You can download the trial version of Easy Karaoke Player freely.
Silverlight is a powerful development platform for creating engaging, interactive user experiences for Web, desktop, and mobile applications when online or offline. This latest version of Silverlight 4 delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers, Microsoft Visual Studio and Microsoft Expression Blend, present the leading edge in rapid, powerful application development. Silverlight 4 Information: This latest version of Silverlight delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers — Microsoft Visual Studio and Microsoft Expression Blend – present the leading edge in rapid, powerful application development. With printing support, rich reporting and charting, and integration with back-end systems and server products including Microsoft SharePoint, Silverlight is ready for business. Silverlight 4 delivers a full suite of powerful capabilities to business application developers, bringing the best-of-breed .NET platform to browser-based experiences. Silverlight provides an ideal platform for developing and deploying modern business applications for both customer facing and staff-facing applications. Business Application Development Silverlight 4 consolidates its position as the natural choice for building business applications on the Web: New Features for Application Developers * Comprehensive printing support enabling hardcopy reports and documents as well as a virtual print view, independent of screen content. * A full set of forms controls with over 60 customizable, styleable components. New controls include RichTextbox with hyperlinks, images and editing and Masked textbox for complex field validation. Enhanced controls include DataGrid with sortable/resizeable columns and copy/paste rows. * WCF RIA Services introduces enterprise class networking and data access for building n-tier applications including transactions, paging of data, WCF and HTTP enhancements. * Localization enhancements with Bi-Directional text, Right-to-Left support and complex scripts such as Arabic, Hebrew and 31 new languages including Vietnamese and Indic support. * The .NET Common Runtime (CLR) now enables the same compiled code to be run on the desktop and Silverlight without change. * Enhanced databinding support increases flexibility and productivity through data grouping/editing and string formatting within bindings. * Managed Extensibility Framework supports building large composite applications. * Exclusive tooling support for Silverlight, new in Visual Studio 2010. Including a full editable design surface, drag & drop data-binding, automatically bound controls, datasource selection, integration with Expression Blend styling resources, Silverlight project support and full IntelliSense. Developer tools * Fully editable design surface for drawing out controls and layouts. * Rich property grid and new editors for values * Drag and drop support for databinding and automatically creating bound controls such as listbox, datagrid. New datasources window and picker. * Easy to pick styles and resources to make a good looking application based on designer resources built in Expression Blend. * Built in project support for Silverlight applications * Editor with full intellisense for XAML and C# and VB languages.
Advanced Task Manager is a program that focuses on keeping your computer secure and helping you find and disable spyware rapidly. Advanced Task Manager shows you exactly what is running on your computer, including the hidden processes. You can view the details of each process, including a security rating and security details such as whether a program connects to the Internet, watches what you type, is an Internet server, is hidden, is encrypted on disk, has invisible windows, etc. The security rating of a program indicates the likelihood of it being a virus, spyware, trojan, etc. If you discover a rogue program you can easily stop, quarantine or uninstall it so it doesn't run anymore. You can also manage your Windows startup programs with the included Startup Manager. Several other tools offer you detailed information about Internet connections, DLL files, CPU and memory use, Internet server programs running on your computer.
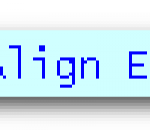
23 Java classes/utilities you can use standalone or embed in your own programs to *commonly known as CSV files. Includes CSVReader, CSVWriter, CSVAlign, CSVChangeCase, CSVCondense, CSVDeDup, CSVDeEntify, CSVDump, CSVEntify, CSVPack, CSVPatch, CSVReshape, CSVSort, CSVSortField, CSVTabToComma, CSVTemplate, CSVToHTML, CSVToSRS, CSVToTable, CSVTuple, LinesToCSV, TableToCSV.
Virtual Drive is a virtual DVD/Blu-ray emulator. It emulates maximum 18 drives and works with DVD/Blu-ray images. For example, to play a Blu-ray backup on PC with PowerDVD 8 or above, you need to use DVD Ripper to backup the Blu-ray to an ISO image file, and use Virtual Drive to mount it, then, PowerDVD will play it. Features Highlight: 1. Emulate maximum 18 drives. 2. Work with both DVD and Blu-ray imagaes. 3. Play a Blu-ray ISO file backup on PC with PowerDVD 8 and above. System Requirements: Windows 7/Vista/XP/2000 (32-bit/64-bit) X86/X64, Pentium II 500 MHz, 256 MB of RAM. For more information about Virtual Drive, please visit www.virtual-drive.org.
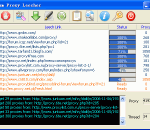
Forum Proxy Leecher (FPL) is an intelligent proxy leecher that can extract proxies from various proxy sites and proxy forums even if the proxies are in the attachment. FPL proxy tester module (Bleach) is specially designed for huge list. It extract the unique proxies from a huge file and rapidly classify them into 3 levels according to their anonymity. Moreover, it's nice that FPL team maintain the leech list and proxyjudge list for you. FPL ensures that it's an easy and amusing work for you to find proxies. We all know that the proxy forums are the best places to gain fresh proxies. But it often takes too much time (more than 50 minutes for 10 forums) to read the new topics and download the attachments. Now FPL does all the dirty work for you. It can automatically extract the fresh proxies for you. If you often need a great amount of fresh proxies, you will probably need it. If you buy proxies from other people, you should try FPL, and perhaps you will eventually be a proxy list seller.
Galactic Reign is a head-to-head game of tactical expansion and conquest. You and your opponent colonize planets, design ships, and build fleets as you fight for domination of the galaxy. Ship design is crucial, as you must predict what their opponent is building and construct ships to counter it. When opposing fleets meet, the battle is rendered on the cloud, showing the result in a stunning cinematic movie.
Farm Frenzy: Pizza Party is a time management and strategy simulation game from MyPlayCity.com, the home of hundreds of great casual games on the Internet. As with all games available at this site, it is the full version, unrestricted and unlimited. There are no demo or trial versions here. Farm Frenzy: Pizza Party will have players handling the entire production process for six types of pizzas, from harvesting grain to shipping goods all around the world. They will need to look after their livestock, producing many different goods for their pizzas. They will need to use upgradable planes and trucks to distribute their products and they will have fifteen upgradable buildings at their disposal. Players will experience the full process from start to finish, becoming dominating businessmen in the industry! The game is hilariously animated, making it particularly fun for people of all ages and also for those who are new to the genre. Learn more and download the game today, completely for free, at homepage
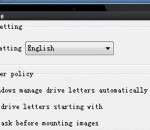
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.