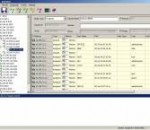
IPMaster is IP address management software. It provides visual IP address assignment (network topology tree), automatic subnet calculator, mask calculation, subnetting, network segment scanning, host monitoring, ping, traceroute, telnet, and netsend etc. It supports VLSM Variable Length Subnet Masks) and CIDR (Classless Inter-Domain Routing). The purpose of this software is to assign and manage IP address efficiently for enterprise network. Key features of IPMaster: 1. Visual IP address management function. 2. Automatic subnetting function. The system provides automatic subnet calculator, at the sub-divisible subnet node, input "Amount of Subnets", "Hosts in each Subnet" or "Subnet Mask", the system will generate child subnet under the target subnet automatically. 3. Manual subnetting function. The system provides manual subnet calculator, at the sub-divisible subnet node, input "IP address", "subnet mask", the system will generate a designated child subnet under the target subnet. 4. Relevant function of host. The system provides 4 default functions - ping, traceroute, telnet and net send, the user can also custom other function. 5. Scan function. The host name, MAC address and user name of all hosts in the target subnet can be got automatically. 6. Monitoring function. The system can monitor the running status of the monitored host, when the host is shutdown, the tip message area would warn by red hints. 7. Search function, the user can search relevant message in the IP address management library by exact search or fuzzy search. 8. Export function, all the information in the IP address management library can be output to a Excel file. 9. Import function, the user can import host information from a Excel file. 10. User-defined host column function, the user can customize the host information column.
What’s new in Version 2013? - Browser Tracking Blocker: Stops over 600 companies from recording your web activities - Website Safety Advisor: Security ratings in your search results—know before you go! - Security for Android: Lost phone recovery, privacy protection and call/SMS blocking - Protection Cloud: Real-time malware classification and extremely fast system scanning - Advanced AntiPhishing: Proactive protection from the craftiest email scams - Social Network Protection: Intelligent parental controls for Facebook and other social sites
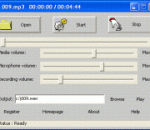
Easy Karaoke Player plays karaoke, records karaoke song to wav file. Easy Karaoke Player can play all kinds of multimedia files with a build-in powerful multimedia player. Easy Karaoke Player plays many audio formats such as MP3, MIDI, KAR, WAV, WMA, AC3, OGG, MPA, MP2, AU, AIF, SND, etc., and video formats VCD, MPEG, AVI, WMV, ASF, OGM, DIVX, DAT, SVCD etc. You can sing your favorite song and record it to high quality WAV file. You can download the trial version of Easy Karaoke Player freely.
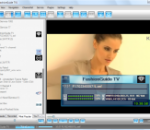
ProgDVB and ProgTV is two is 2 independent user interfaces which can work together from one folder at one list of channels, settings etc. ProgTV is aimed at use with remote control(HTPC). ProgDVB contains more functions but is intended for use by a mouse. Thus it is very convenient to use both interfaces. ProgDVB is a piece of software which allows you to watch SAT-Television and listen to Radio channels directly from satellite by using DVB-PCI cards with hardware decoders on the board, SAT-dish, and personal x86-compatible computers. Support for various types of data sources: * Internet TV and Radio. About 4000 channels in the list. * DVB-S (satellite), DVB-S2, DVB-C (cable), DVB-T, ATSC, ISDB-T * IPTV * Analog TV * Playback from a file Main functions: * High Definition TV support including H.264/AVC * Picture-in-picture support as well as independent simultaneous recording/playback of several channels from one or more devices * Support for the majority of DVB, ISDB-T and ATSC devices including DiSEqC and CAM interfaces support * Support for all digital TV audio formats: MPEG, AC3, AAC,... * Time shifting functionality using the RAM or disk buffer of unlimited size * 10 Bands equalizer * TV and Radio channels recording * Playback from disk based files * Electronic program guide (EPG) from Digital TV or XmlTV,JTV. * Teletext * Subtile(Teletext, image-based and closed captions) * Support for VR, VMR7,VMR9 and EVR renderers including OSD (except VR) independently from channel type or signal presence * Network broadcasting * Skins for OSD and GUI * Both Win32 and full-fledged Win64 versions are available * Interface Language Localizations Currently works with DVB-S, DVB-S2, DVB-T and DVB-C cards of the following manufactures: * Anysee (E30S Plus,...) * AverMedia DVB-S * Azurewave (TwinHan) (VP-1027, VP-1034, VP-1041,... ). * BroadLogic 2030/1030 * Compro VideoMate DVB-S * Digital everywhere FireDTV/FloppyDTV * DVBWorld USB2.0 DVB-S/DVBWorldDTV(PCI-Sat), Acorp TV878DS/DS110/DS120, Nextorm NBS240/NSC120 * GeniaTech products(Digistar DVB-S PCI, satbox, TVStar, Digistar2, Digiwave 103G,...) * Hauppauge * Kworld DVB-S 100 compatible (Vstream, Dynavision..... ) * LifeView FlyDVB * 10moons * Netcast DVB * NEWMI Advanced DVB * Pinnacle * Technotrend * Tevii * TBS Q-Box * Technisat * Telemann Skymedia 300 DVB (not official) * Tongshi * Terratec * St@rKey usb box * Cards with BDA driver (possible issues with some cards) * Also works without a card, for example, as a video player or as a broadcast client
Silverlight is a powerful development platform for creating engaging, interactive user experiences for Web, desktop, and mobile applications when online or offline. This latest version of Silverlight 4 delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers, Microsoft Visual Studio and Microsoft Expression Blend, present the leading edge in rapid, powerful application development. Silverlight 4 Information: This latest version of Silverlight delivers hundreds of features and controls that, when combined with the continued innovation in Microsoft’s world-class tools for designers and developers — Microsoft Visual Studio and Microsoft Expression Blend – present the leading edge in rapid, powerful application development. With printing support, rich reporting and charting, and integration with back-end systems and server products including Microsoft SharePoint, Silverlight is ready for business. Silverlight 4 delivers a full suite of powerful capabilities to business application developers, bringing the best-of-breed .NET platform to browser-based experiences. Silverlight provides an ideal platform for developing and deploying modern business applications for both customer facing and staff-facing applications. Business Application Development Silverlight 4 consolidates its position as the natural choice for building business applications on the Web: New Features for Application Developers * Comprehensive printing support enabling hardcopy reports and documents as well as a virtual print view, independent of screen content. * A full set of forms controls with over 60 customizable, styleable components. New controls include RichTextbox with hyperlinks, images and editing and Masked textbox for complex field validation. Enhanced controls include DataGrid with sortable/resizeable columns and copy/paste rows. * WCF RIA Services introduces enterprise class networking and data access for building n-tier applications including transactions, paging of data, WCF and HTTP enhancements. * Localization enhancements with Bi-Directional text, Right-to-Left support and complex scripts such as Arabic, Hebrew and 31 new languages including Vietnamese and Indic support. * The .NET Common Runtime (CLR) now enables the same compiled code to be run on the desktop and Silverlight without change. * Enhanced databinding support increases flexibility and productivity through data grouping/editing and string formatting within bindings. * Managed Extensibility Framework supports building large composite applications. * Exclusive tooling support for Silverlight, new in Visual Studio 2010. Including a full editable design surface, drag & drop data-binding, automatically bound controls, datasource selection, integration with Expression Blend styling resources, Silverlight project support and full IntelliSense. Developer tools * Fully editable design surface for drawing out controls and layouts. * Rich property grid and new editors for values * Drag and drop support for databinding and automatically creating bound controls such as listbox, datagrid. New datasources window and picker. * Easy to pick styles and resources to make a good looking application based on designer resources built in Expression Blend. * Built in project support for Silverlight applications * Editor with full intellisense for XAML and C# and VB languages.
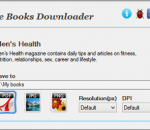
FSS Google Books Downloader is a free utility that allows users to download books from Google Books Search and convert them to PDF, JPG or PNG. Using FSS Google Books Downloader you can download millions of books from libraries and publishers worldwide completely free!
This is an adventure game where you are Ben 10. Your cousin Gwen has disappeared and you investigate the case trying to find her. You'll need to talk to different people, find objects and figure out what to do to proceed. Sometimes you'll be asked to play a mini game like pressing the arrows that appear on the Omnitrix or similar.
All-in-one platform for developing any types of Office extensibility projects, including COM add-ins, smart tags, RTD servers and user-defined functions for Microsoft Office 2010 - 2000. Create application-specific plugins and shared extensions that work on all end-user applications: Outlook, Excel, Word, PowerPoint, Visio, Project, MapPoint, Publisher, etc. in C#, VB.NET, C++ and Delphi Prism. More info: homepage
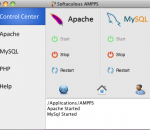
AMPPS is a stack of Apache, PHP, MySQL, Perl & Python. AMPPS enables you to focus more on using applications rather than maintaining them. With AMPPS you can create a website by installing any of the 300+ Apps, customizing it, and then simply publishing it on the internet via a wide choice of hosting service providers.
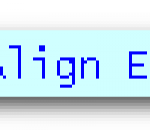
23 Java classes/utilities you can use standalone or embed in your own programs to *commonly known as CSV files. Includes CSVReader, CSVWriter, CSVAlign, CSVChangeCase, CSVCondense, CSVDeDup, CSVDeEntify, CSVDump, CSVEntify, CSVPack, CSVPatch, CSVReshape, CSVSort, CSVSortField, CSVTabToComma, CSVTemplate, CSVToHTML, CSVToSRS, CSVToTable, CSVTuple, LinesToCSV, TableToCSV.
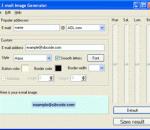
Spam messages can be called the scourge of all Internet users nowadays. According to recent studies, half of email messages received by active users are spam messages, which results in a number of undesirable consequences for companies, from increased overheads due to extra time spent for processing spam to direct damage of the IT infrastructure because of malware, high traffic and other factors. Several methods have been developed to keep users' email addresses secret, the most efficient one being quite obvious - never to leave your address in a text form on forums, in blogs and personal pages, where it can be automatically scanned and recognized by spambots. If you have been seeking an easy-to-use and affordable tool that will allow you to dramatically decrease your exposure to spambots and help you fight spam in your inbox, make sure you don't miss Sibcode E-Mail Image Generator! The program is based on a fairly simple principle - it enables you to generate email images that can be used as a substitute for your email address anywhere. Images can be easily read by other people while being totally inaccessible to spammers' email harvesting programs, which ensures that your email will not appear on spam lists. E-Mail Image Generator offers users the following features: - Protection from automated email grabbers on your site - The ability to create attractive buttons - The ability to create aqua-style email images - Templates for major online email services - 30-day money back guarantee Using the program is easy as 1-2-3: enter your email address and the program will generate a button for it. You can then place the button anywhere - your forum signatures, you personal blog page or your web page. These simple steps will help you avoid undesired exposure to spammers' email extraction tools and reduce the number of useless messages in your inbox. Reliable spam protection at an affordable price - that's all Sibcode E-Mail Image Generator is about!
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.