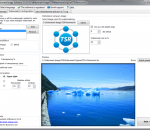
Protect your photos with the TSR Watermark images software that can run in batch mode. Add multiple watermarks in one run, and save each watermarked image at multiple locations with diferent setttings, add logo or text as watermark to your pictures, images, photos or other digital images. Batch processing when creating watermark. Transparent or solid watermark. 3D watermark effect using emboss bump mapping. Free software for personal use, to add watermark to pictures. How to watermark photos, use this software. Latest version includes angled text used for watermarking. Keep the EXIF information when saving jpeg photos, set the quality of jpegs, select the output image type (jpeg, png, gif, bmp, tiff). Automatically rotate the resulting image, based on the orientation tag in the EXIF information in the photo. Add copyright text to the EXIF information. Automatic preview the selected preview photo when changes are made to the setup. Create text watermarks with either embossed or chiseled text for a cool 3D effect! TSR Watermark Images Software is available in multiple languages, currently translated languages is English, German, Italian, Japanese, Hungarian, Czech, Spanish, French, Romanian, Dutch, Vietnamese, Portuguese (Brazil & Portugal), Chinese (Simplified & Traditional), Indonesian, Russian and Danish
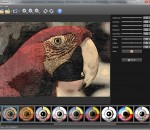
XnSketch allows you to turn your photos into cartoon or sketch images. Features: 18 different effects (black strokes, white strokes, pastel, pencil sketch, colored sketch, ...) Edge strength, and opacity adjustement Contrast, brightness, saturation adjustement Save or share the result
TeamViewer Portable addresses the needs of people who travel frequently and want to use TeamViewer from different, always changing computers. TeamViewer Portable can be started directly from the USB stick, gets it's licensing from an .ini file on the stick and does not leave any traces on the computer where you use it, e.g. no registry values are stored there. FEATURES: Remote Control without Installation: · With TeamViewer you can remotely control any PC anywhere on the Internet. No installation is required, just run the application on both sides and connect - even through tight firewalls. Remote Presentation of Products, Solutions and Services: · The second TeamViewer mode allows you to present your desktop to a partner. Show your demos, products and presentations over the Internet within seconds - live from your screen. File Transfer: · TeamViewer comes with integrated file transfer that allows you to copy files and folders from and to a remote partner - which also works behind firewalls Works behind Firewalls: · The major difficulties in using remote control software are firewalls and blocked ports, as well as NAT routing for local IP addresses. · If you use TeamViewer you don't have to worry about firewalls: TeamViewer will find a route to your partner. Highest Security Standard: · TeamViewer is a very secure solution. The commercial TeamViewer versions feature completely secure data channels with key exchange and RC4 session encoding, the same security standard used by homepage No Installation Required: · To install TeamViewer no admin rights are required. Just run the software and off you go... High Performance: · Optimized for connections over LANs AND the Internet, TeamViewer features automatic bandwidth-based quality selection for optimized use on any connection.
All-in-one platform for developing any types of Office extensibility projects, including COM add-ins, smart tags, RTD servers and user-defined functions for Microsoft Office 2010 - 2000. Create application-specific plugins and shared extensions that work on all end-user applications: Outlook, Excel, Word, PowerPoint, Visio, Project, MapPoint, Publisher, etc. in C#, VB.NET, C++ and Delphi Prism. More info: homepage
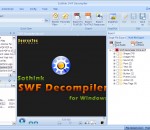
Leading Flash decompiler and Flash to html5 converter. Converts SWF to HTML5/FLA/FLEX. Easily extracts Flash resources like shape, image, sound (mp3, wav), video (flv), text, sprite, ActionScript, etc; Imports SVG & edits shape elements; Replaces image/ text/sound elements; Supports Flash CS3/CS4/CS5/CS6 and ActionScript 2.0/3.0; Able to get XFL file from Flash CS5 SWF; Exports SWF resources in batch; One-click online Flash capture and download.
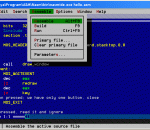
The Netwide Assembler, NASM, is an 80x86 and x86-64 assembler designed for portability and modularity. It supports a range of object file formats, including Linux and *BSD a.out, ELF, COFF, Mach-O, Microsoft 16-bit OBJ, Win32 and Win64. It will also output plain binary files. Its syntax is designed to be simple and easy to understand, similar to Intel's but less complex.
Expand your building empire from the sunny coasts of Florida to the snowy lands of Alaska in Virtual City 2: Paradise Resort! Take on unique missions and complete special goals to earn more money and upgrade your cities. Construct a casino, spruce up a ski resort, indulge in an Ice Hotel, and much more in this incredible Strategy game!
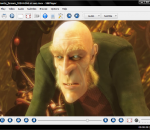
The award-winning OpenSource media player available for Windows now! The MPlayer for Windows package contains the most recent builds of MPlayer for the Windows platform as well as SMPlayer and MPUI MPlayer for Windows provides native support for more than 192 Video and 85 Audiocodecs. For maximum performance, the installer includes optimized builds for different CPU types. Furthermore the Full-Package includes the Binary Codec Package, while the Light-Package does not. This package contains the latest builds of MPlayer for the Windows platform as well as SMPlayer and MPUI. Thanks to the award-winning MPlayer engine, more than 192 Video- and 85 Audiocodecs are supported natively! For maximum performance the package includes optimized MPlayer binaries for various CPU types. Furthermore the Full-Package includes the Binary Codec Package to enable even more audio/video formats. Everything in one self-contained download :-) The Light-Package is a stripped-down version of this package, that includes MPUI and the MPlayer binaries only. Features: · The award-winning OpenSource Media Player "MPlayer" available for Windows now! · Self-contained "all-in-one" installer (made with NSIS) · More than 192 Video- und 85 Audiocodecs supported natively! (-> details) · Latest optimized MPlayer builds by Celtic Druid · Improved version of MPUI front-end (compiled with Delphi7 Professional) · Binary Codec Package for Windows (included in Full-Package only) · Full multi-language Unicode support (more than 20 languages to choose) · Optimized builds for: Athlon-XP, Athlon-64, Core 2, Pentium-4, Pentium-4 Precott, Pemtium-M · Generic build that runs on all CPUs (Runtime Detection)
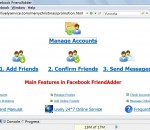
Facebook FriendAdder(FFA), the most professional facebook automation tool, it is the dream of facebook marketers who are making full use of it will probably benefit a lot. Internet marketers are experiencing a gold rush of web 3.0 FREE advertising to highly targeted leads on the fastest growing social network "Facebook". Facebook FriendAdder is an automation marketing tool for facebook marketers. Facebook FriendAdder can spare no effort to help you to grow your business and achieve success. With Facebook FriendAdder, you can + manage THOUSANDS of facebook accounts + manage proxies and auto assign them to facebook accounts + check account infromation+bypass login problems + send mass facebook friend requests to targeted people + confirm mass facebook friend requests from friends+ send mass facebook friend messages to targeted people + delete mass received messages and pending friend requests. Do not worry about changes on facebook, free lifetime update is available and 23 well-trained members are 24*7 online to offer support. Do not worry about buying an unsuitable software, 3 times free trials for you to experience all features of the software and we promise 30 days money back guarantee without any condition.
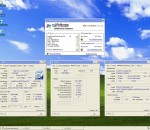
wPrime is a compact and portable application that offers users two modes for testing the capabilities of their computer's CPU.The interface is based on a simple and minimalistic window, where wPrime gets started by retrieving hardware information from your PC, thus revealing the CPU specs, core, revision, clock, cache, VCore, FSB, motherboard model and vendor, together with the memory type, size, clock and timings.
Galactic Reign is a head-to-head game of tactical expansion and conquest. You and your opponent colonize planets, design ships, and build fleets as you fight for domination of the galaxy. Ship design is crucial, as you must predict what their opponent is building and construct ships to counter it. When opposing fleets meet, the battle is rendered on the cloud, showing the result in a stunning cinematic movie.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.