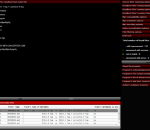
Converts the audio of the audio or video files given at input, normalizes its volume (so that they all present the same maximum volume), and converts the resultant audio to mp3. The resultant files can have its metadata edited (ID3 tags) at will. The configurations are profile based, in order to make the batch job easier to configure - the audiophile profile is selected by default. The program is portable - it can be run from a pen drive.
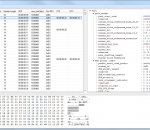
MPEG PS Utils application provides the user with a visual representation of the multiplexed stream structure of MPEG-2 Program Streams (ISO/IEC 13818-1). The application allows the user to investigate the basic program stream packets with their fields. The application also allows the user to manipulate with program streams by demultiplexing to PES and ES streams.
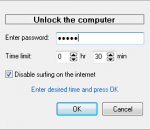
Time Lock is a simple program, which allows to protect your computer against unwanted use. When the computer is locked by the Time Lock software, nobody can access documents on your computer, run programs, browse on the internet, etc. Time Lock is very often used by parents as a "child lock" for home PC. Simply let your child to play games or browse on the internet only for a certain time period.
The free Svchost Process Analyzer examines all Svchost instances. This makes it easy to recognize processes that start up through Svchost and disguise their activities. This was the way the Conficker Worm, which infected millions of computers, operated. The genuine Svchost.exe is an important Windows system process and is located in the C:WindowsSystem32 directory. The Svchost.exe processis often misused by spyware, Trojans or worms.
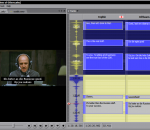
titlebee offers a unique and fast way to create video titles for embedding in your videos or importing into your video editor software. Features include: Timeline Editing, Just-in-time Titles, Typography, Title Manipulation, Side-by-side Tracks, Multilingual, Any Video Format, Time Control, Quick Spotting, Text Export, NLE Overlay Import, Hardsubbing, Bookmarking, Synchronization, Cloud Backup
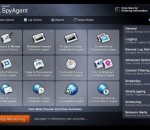
SpyAgent integrates seamlessly with SpyAnywhere, allowing you to gain total control of the remote PC with SpyAgent and SpyAnywhere. SpyAnywhere allows you to view and manage all of SpyAgent's activity logs; as well as view the remote user's keystrokes in real-time, view screenshots of the desktop, browse the remote file system, and more!
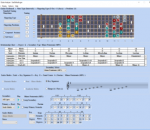
Ultimate Scale Mastery - Learn What Fits Into What & Where - Everywhere! Create a clear mind map of what fits into what and where by matching scales and arpeggios through a harmony relationship chart. Matching secondary scale and arpeggio formula octaves are displayed with a bordered note to see how they fit inside the primary scale. Practice and break down guitar scales with the largest scale fingering selection database that is unmatched.
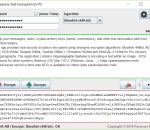
Keep your notes, messages (SMS, emails, ...), cryptocurrency keys (seeds, mnemonics), and other texts safe from all unwanted readers. Texts are encrypted using strong encryption algorithms: AES (Rijndael) 256bits, Serpent 256bit, Blowfish 448bit, Twofish 256bit, ... ciphers are available. A steganography function using F5 alg. is included. Compatible with P.T.E. for iOS and S.S.E. for Android: more on homepage
Passwordstate is an on-premise web based solution for tracking both passwords for individuals, and Shared Password Lists for teams of people. Passwordstate can scale from a single user to the enterprise, and with secure access control over Shared Password Lists, Passwordstate is the enterprise password manager of choice. Passwordstate has International support and can be used in all English speaking countries.
NowSmart Talkin is designed for recording from Speakers and Microphone at the same time. It is easy to record your voice over background music. If you are looking for a Call Recording Software, NowSmart Talkin is also a good choice. It works directly with sound card, so there is no software compatibility problem, you do not need to worry about what voice chat software you are using, and which verison of it you are using.
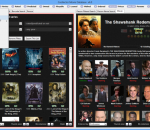
Coollector Portable Movie Database is an easy-to-use application that will help you browse a huge movie database. Personalize it, with your possessions and taste. Movies that you own have their title underlined. Colored icons show if you liked or disliked a movie.
GOM Media Player The only media player you need - for FREE! Not only is GOM Media Player a completely FREE video player, with its built-in support for all the most popular video and Media Player formats, tons of advanced features, extreme customizability, and the Codec Finder service, GOM Media Player is sure to fulfill all of your playback needs. With millions of users in hundreds of countries, GOM Media Player is one of the world`s most popular video players. Whats New : Added "Touch Setting" feature for touch screen devices. Added "Search box" feature on playlist. (Ctrl+F) Supported "HTTPS URL" for youtube or net radio playback. (Ctrl+U) Added "Music Tap" on preferences related to play music files. Improved performance related to "speed of add & delete" of files on playlist. Other miscellaneous corrections, fixes, and changes
Iperius Backup is one of the best free backup software, also released in commercial editions for those who need advanced backup features for their companies. The freeware version of Iperius Backup allows you to backup to any mass storage device, such as NAS, external USB hard drives, RDX drives, and networked computers. It has comprehensive scheduling and e-mail sending functions. It supports zip compression with no size limit, incremental backup, network authentication and the execution of external scripts and programs.
Maryfi is a free and easy to use software router for Windows 7, 8 , and 8.1 computers. With Maryfi, users can wirelessly share any Internet connection such as: a cable modem, a cellular card, or even another Wi-Fi network. Other Wi-Fi enabled devices including laptops, smart phones, music players, and gaming systems can see and join your Maryfi hotspot just like any other Wi-Fi access point and are kept safe and secure by password-protected WPA2 Encryption.